ARTICLES
How to secure your remote applications
- 3 minutes read - 542 wordsI am writing this around the time where we are at the beginning of a global pandemic. Everyone is trying to figure out how to keep their business up and running during this challenging period. Most of the employers have mandated work from remote policy. One of the main challenges is how to connect to your applications remotely. Traditionally the answer is VPN. There are so many challenges wrt scalability, availability, and performance of these traditional VPN software. Don’t worry, there are alternatives.
Here I am going to explain the setup that I have used to secure my application using Cloudflare Access, which provides Simple, secure access for internal apps. Check out the link which provides a great explanation on how Access works. Also, another good news is that this product is completely free (at least for the next 6 months due to the outbreak of COVID-19). Yes, you read it right. Honestly, this is a massive news. Here is an excerpt from the announcement.
If you are not yet using Cloudflare for Teams, and if you or your employer are struggling with limits on the capacity of your existing VPN or Firewall, we stand ready to help and have removed the limits on the free trials of our Access and Gateway products for at least the next six months.
I always wanted to try how Access works and there can’t be a better time than now to try. Here is the simple 4 steps which I did to get up and running:
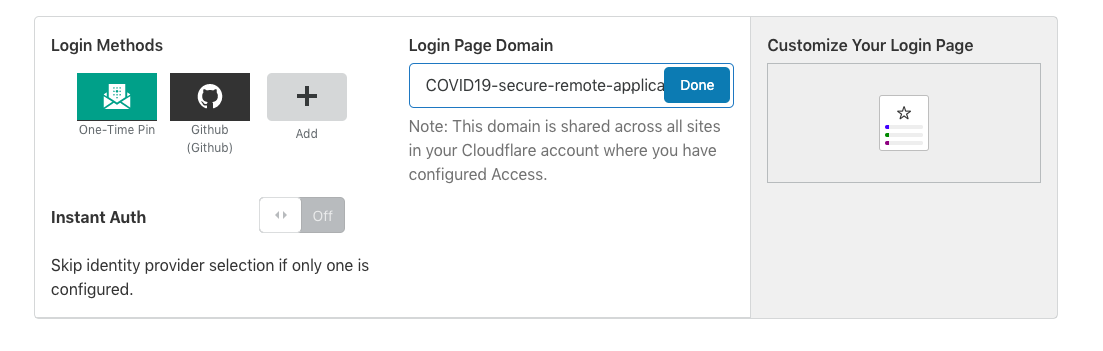
Select an Identify provider: Identity provider is nothing but an authentication method that your end user is going to be authenticated. It can be your existing identity provider such as Gmail, Facebook, Github. Of course, you can also use Okta, AzureAD but thats available for enterprise plan. I have chosen One-Time pin, and Github.
Get a Login Page Domain: Here is what I created for this demo. covid19-how-to-secure-remote-application.cloudflareaccess.com. Feel free to click, I assure there is no catch.
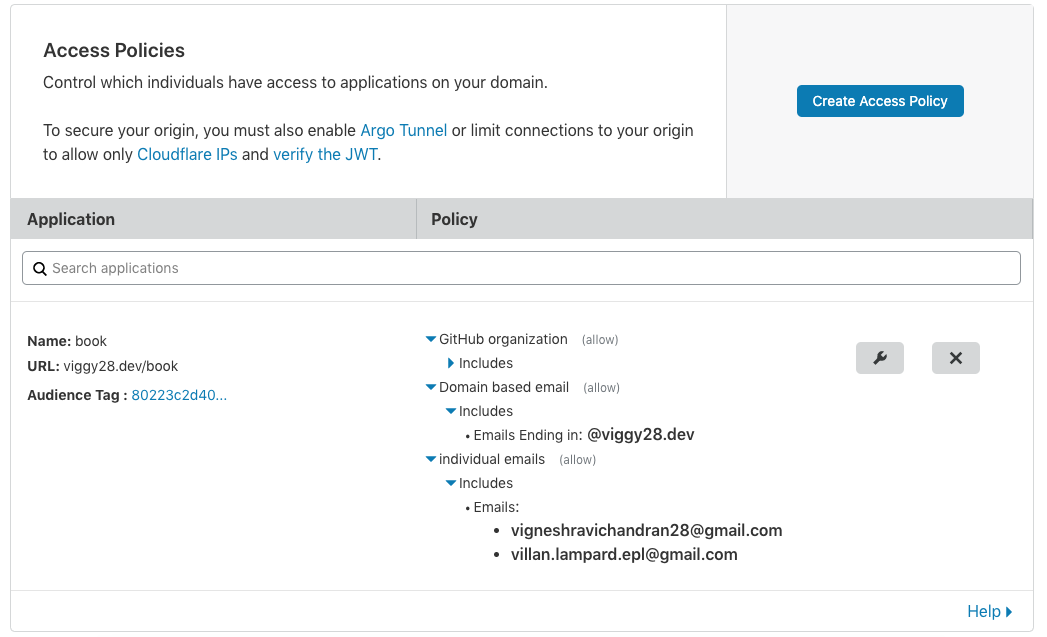
Set up an Access Control Policy: Access-control List defines who can do what. Similar to authorization in the databases.
- Provide a suitable Application Name.
- Specify the domain where your application is hosted on. For example, mine runs on viggy28.dev/book
- I have added Github organization, emails from a specific domain
and individual emails as a different authentication method to
reach my application. There are other ways like IP ranges. This
shows how granular you can get into when it comes to policies.
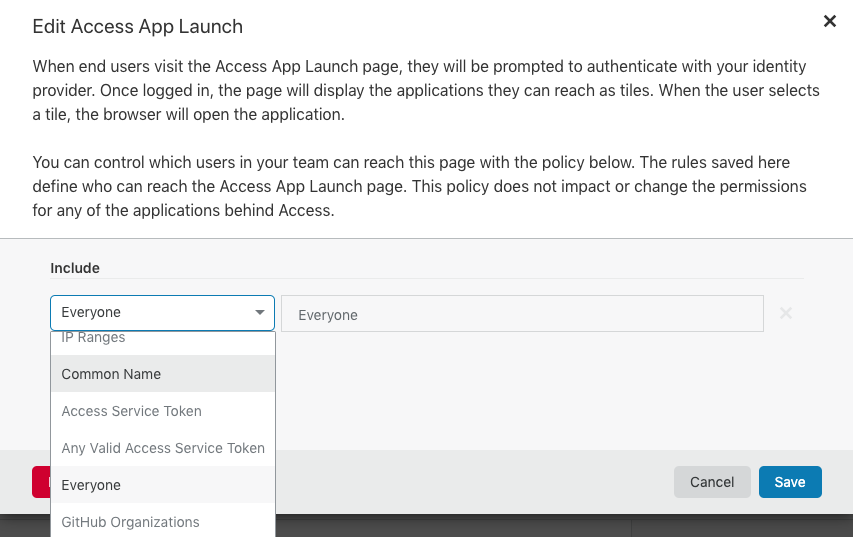
Access App Launch: We are almost there. I have set it up as Everyone to access the App. Since I have secured it using ACL in the above step I am not concerned about anyone trying to reach my application. If you want you can still use the same authentication methods used as your Identity Provider.
That’s it !!! Check out your app access URL. Mine is https://covid19-how-to-secure-remote-application.cloudflareaccess.com/
I am using the One-Time pin Identity provider method to authenticate.
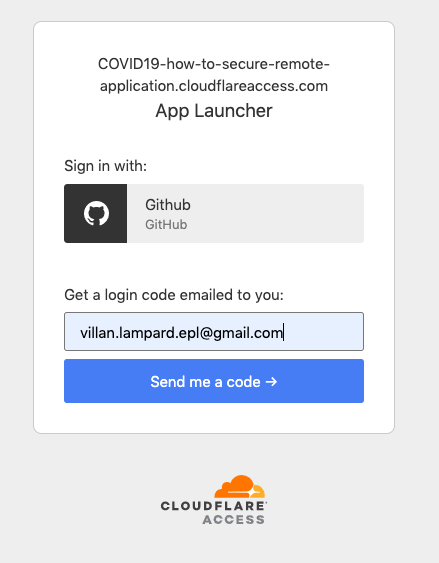
That email address is already added to our access policy. So I did get a 6 digit pin within a minute to that email! email.
Note: Not only HTTP based application, you can also secure SSH, RDP based applications. Access with Gateway one can build a fully fledged VPN.